An adaptive predefined time sliding mode control for uncertain nonlinear cyber-physical servo system under cyber attacks
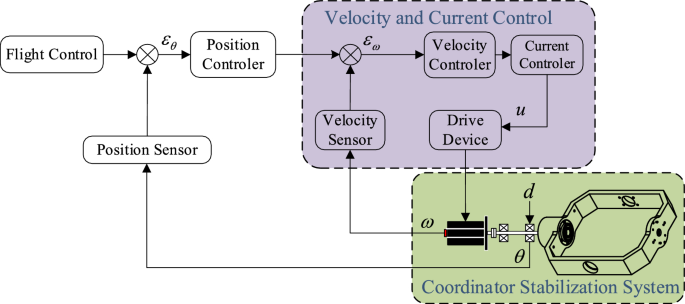
We are going to present and analyze the results of our simulation experiments in this Section, with an emphasis on the effectiveness of the suggested PTCSMAC in the context of a seeker coordinator CPS servo system. First, as shown in Fig. 3, the demonstration of ELM and then we can use that to obtain the PTCSMAC’s general control structure. After then, the conversation will shift to a thorough analysis of the system’s parameters and how they interact with the requirements of the suggested controller to affect overall performance. Overall control CPS servo position control system is sown in Fig. 4.
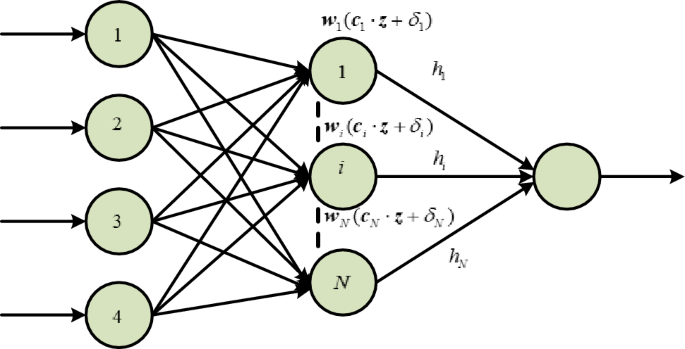
ELM basic structure diagram.
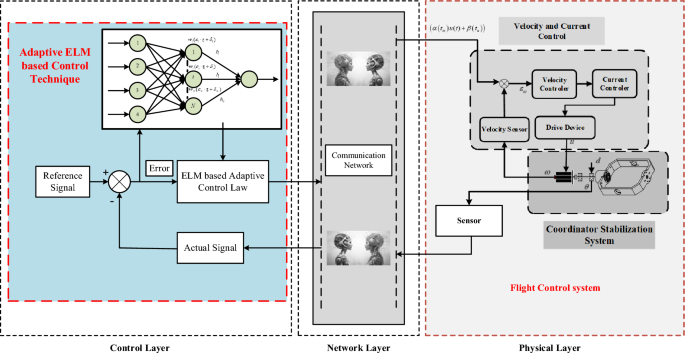
Overall control structure of the proposed PTCSMAC.
This section also aims to validate the PTCSMAC’s performance across different operational conditions, ensuring that it meets the high-precision control demands of the CPS seeker servo system, particularly its response to the reference position signal and resilience to different level of cyber-attacks as well as potential disturbances. The practical Seeker Coordinator Servo System Parameters are demonstrated in the following Table 1.
We have taken the following parameters for the controller settings as depicted in Table 2 and these gains as well as settings will remains unchanged in all the cases as discussed below. Some of the parameters such as predefined time and activation function has been changed according to simulation experiment in order to analyze the effectiveness of our proposed control technique (PTCSMAC).
Case 1: attack free (attack free scenario)
In this section, we have analyzed and explained the simulation results, which demonstrate the effectiveness of our proposed control technique (PTCSMAC), in the context of a normal case when cyberattack does not occur. Furthermore, we have also covered these aspects: position tracking accuracy, tracking error and control effort of our proposed control technique (PTCSMAC).
$${\text{Case1}}:{\text{ attack free scenario}}\left\{ \begin{gathered} \alpha \left( {t_{m} } \right) = 1 \hfill \\ \beta (t_{a} ) = 0 \hfill \\ \end{gathered} \right.$$
The performance of the proposed PTCSMAC control technique in an attack-free case is thoroughly evaluated in Fig. 5, which is represented by three subfigures that each represent a distinct feature of system behavior.
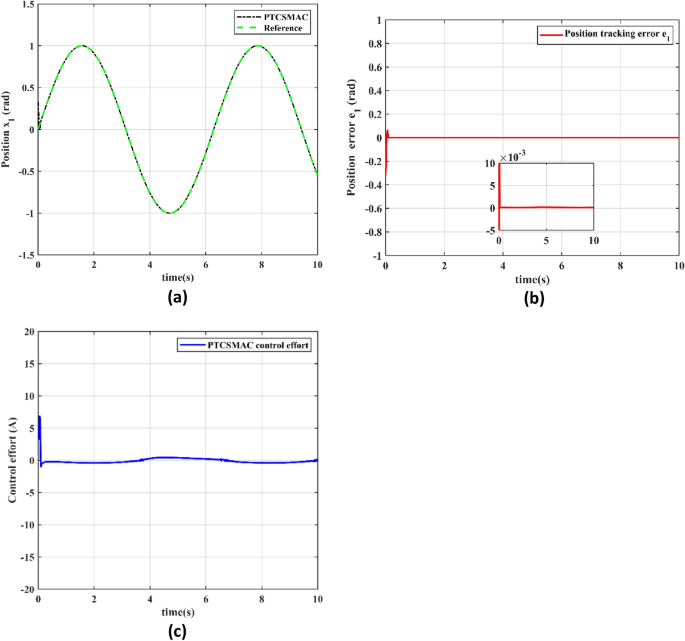
Proposed control tracking performance. (a) Reference position v/s output position trajectory tracking (black line is our proposed PTCSMAC control while the red line is given reference). (b) Position tracking error (red line is error under our proposed PTCSMAC. (c) Control effort of our proposed PTCSMAC.
Figure 5a illustrates the tracking between reference position trajectory and the output position trajectory, where the red line signifies the given reference trajectory and the black line represents the system’s response when under our proposed PTCSMAC control. The position tracking suggests that our proposed PTCSMAC control law can achieve perfect tracking, which precisely follows the given reference position. Figure 5b demonstrates the error of the position tracking. The red line, which shows the error under our proposed control (PTCSMAC), is seen to be quite small and goes up to the micro level, highlighting the control technique’s accuracy. For systems that require precise control, a small error margin indicates that the system can track the reference signal very precisely and with a high degree of accuracy. Figure 5c, deals with the control effort that the PTCSMAC demands. Our proposed PTCSMAC appears to function effectively without requiring significant or abrupt changes in control signals, based on the representation of a steady and smooth control effort. This type of smooth control effort is a sign of a reliable control system that can continue operating without straining the actuators or using too much energy. Our proposed PTCSMAC control shows an excellent performance with perfect tracking, minimum error, and a smooth control effort in Case 1, which is free from any attacks, highlighting its effectiveness and reliability under ideal conditions.
Case 2: low level attack
In this section, we are going to analyze and explain the research results, which compares the effectiveness of three control techniques, including our proposed novel approach (PTCSMAC), in the context of a low-level cyberattack. This analysis has covered three comparative aspects: position tracking accuracy, tracking error and control effort.
$$\left\{ \begin{gathered} \left. \begin{gathered} \alpha \left( {t_{m} } \right) = 1 \hfill \\ \beta (t_{a} ) = 0 \hfill \\ \end{gathered} \right\}\,\,\,,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,t < 2 \hfill \\ \left. \begin{gathered} \alpha \left( {t_{m} } \right) = 0.5 + 0.5.e^{(0.1t)} \hfill \\ \beta (t_{a} ) = 0.5\cos^{2} \left( {x_{2} } \right) \hfill \\ \end{gathered} \right\}\,,\,\,\,2 \le t \le 5 \hfill \\ \left. \begin{gathered} \alpha \left( {t_{m} } \right) = 0.03 + 0.01.e^{(0.1t)} \hfill \\ \beta (t_{a} ) = 0.1\cos^{2} \left( {x_{2} } \right) \hfill \\ \end{gathered} \right\},\,\,\,other\, \hfill \\ \end{gathered} \right.$$
For case 2 and Fig. 6 have thoroughly examined the performance of three control techniques in terms of position tracking accuracy and control effort, particularly under conditions of multiple uncertainties and cyberattacks as well as shows the tracking errors. In this study, Fig. 6a shows the resilience of the proposed control system under challenging conditions by comparing the performance of three different control strategies under low-level attacks (Case2). The newly proposed predefined time convergence sliding mode adaptive controller (PTCSMAC), shown as a blue line on the graph, is the main subject of discussion. This line shows the system’s output location, which is influenced by several uncertainties and malicious attacks, but nevertheless closely tracks the reference position trajectory. PTCSMAC’s performance is compared to two other control approaches found in the literature: Ming Chen et al.’s method (green line) and Zhirun Chen et al.’s method (red line). It is demonstrated that the tracking performance of Ming Chen et al.’s method is not optimal, making it inadequate for precision control. However, under the identical conditions, Zhirun Chen et al.’s control technique encounters severe singularity problems, which results in a complete failure to track the target trajectory. In conclusion, Fig. 6a clearly shows how the PTCSMAC works better than the approaches which have been compared, maintaining precision and reliability in position tracking even in the case of a system compromise, making it a notably advantageous approach in the face of challenges like cyberattacks and uncertainty.
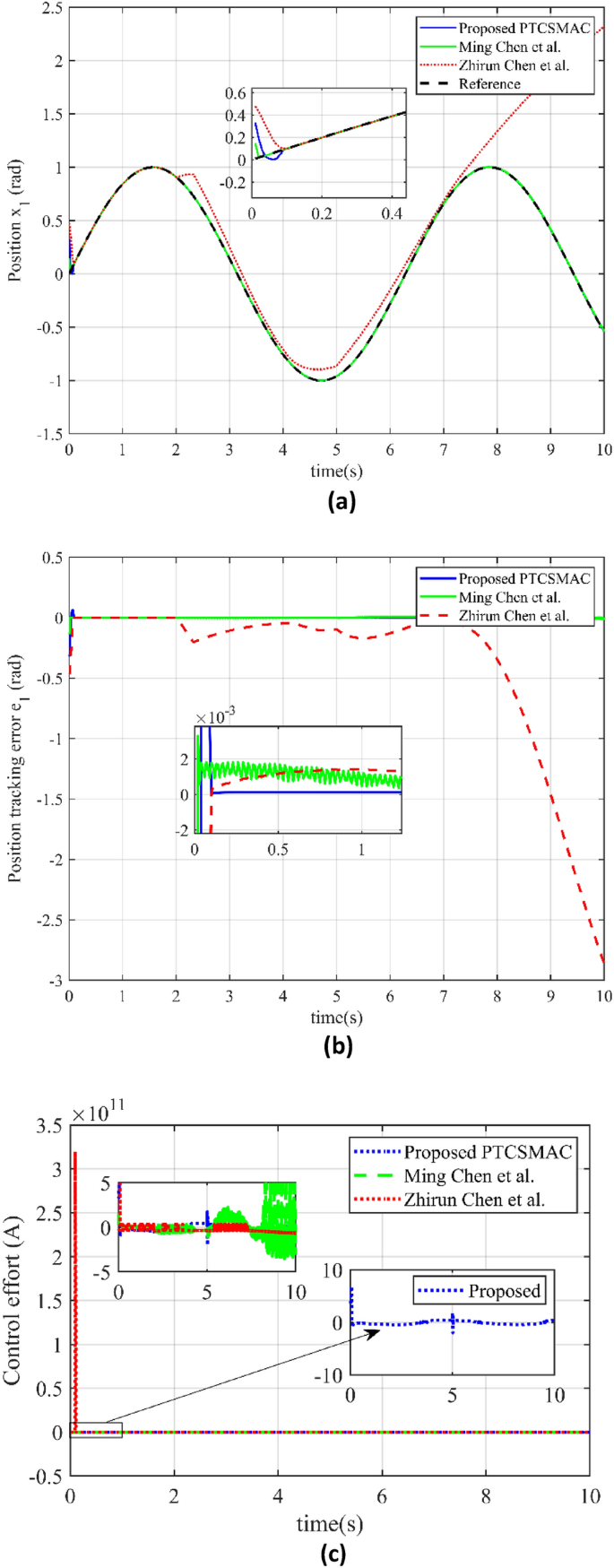
Comparison of tracking and control performance in case 2. (a) Reference position v/s output position trajectory tracking (blue line is our proposed PTCSMAC control tracking, red line is the tracking of Ref39, while green line is the tracking of Ref37). (b) Position tracking error comparison (blue line is our proposed PTCSMAC, red line is the tracking error of Ref39, while green line is the tracking error of Ref37). (c) Control effort comparison of different control laws (blue line is our proposed PTCSMAC control law, red line is the control effort of Ref39, while green line is the control effort of Ref37).
Figure 6b offers a comparison of position tracking errors. The blue line represents the error for the proposed PTCSMAC, showing significantly smaller deviations from the desired position, which suggests a high level of precision in tracking. While the red and green lines represent the tracking errors for the control techniques by Zhirun Chen et al. and Ming Chen et al., respectively. Zhirun Chen et al.’s method, as indicated by the red line, has pronounced tracking errors due to singularity issues that arise amongst uncertainties and cyberattacks, rendering it ineffective. Ming Chen et al.’s method, although fair in position tracking, is depicted by the green line and is characterized by a large tracking error, which reduces its reliability for precise control.
It can be seen from Fig. 6c which depicts the control effort exerted by the different control laws. The blue line for the PTCSMAC indicates a controlled and stable effort, which implies efficiency and reliability without excessive demand on system resources. In contrast, Ming Chen et al.’s method (green line) shows a high level of chattering in the control input, a phenomenon that can lead to premature wear and tear or damage to the actuators within the control system. As compared to the technique by Zhirun Chen et al. (red line), the control effort fails when it faces the cyberattacks due to the same singularity issues that affect its tracking ability, which could lead to system instability or failure. As we can see from Fig. 6c which highlights the superiority of our proposed PTCSMAC, that not only maintains a high reliability in tracking the desired trajectory but also operates with an efficient control effort. In a contrast with the other methods that struggle with large errors, system inefficiencies, and potential damage to the control system components, especially in the face of cyber-attacks and uncertainties.
Case 3: high level attack
In this section, similar to above case 2, we are also analyzing and describe the rigorous results, in which we will compare the efficacy of different proposed control laws in different existing literature, with our proposed approach (PTCSMAC). In this section we will discuss worst case scenario the high-level cyberattack. Similarly, we will cover three comparative aspects: position tracking accuracy, tracking error and control effort in this worst case.
$${\text{Case3}}:{\text{ The worst-case scenario}}\left\{ \begin{gathered} \left. \begin{gathered} \alpha \left( {t_{m} } \right) = 1 \hfill \\ \beta (t_{a} ) = 0 \hfill \\ \end{gathered} \right\}\,\,\,,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,\,t < 2 \hfill \\ \left. \begin{gathered} \alpha \left( {t_{m} } \right) = 5 + 10.e^{(0.1t)} \hfill \\ \beta (t_{a} ) = 10.\cos^{2} \left( {x_{2} } \right) \hfill \\ \end{gathered} \right\}\,,\,\,\,2 \le t \le 5 \hfill \\ \left. \begin{gathered} \alpha \left( {t_{m} } \right) = 1 \hfill \\ \beta (t_{a} ) = 0 \hfill \\ \end{gathered} \right\}\,\,\,,\,\,\,other\, \hfill \\ \end{gathered} \right.$$
In Fig. 7, we have investigated the performance of three different control techniques under a high-level cyber-attack scenario, offering a detailed assessment of their robustness and practicality in maintaining system control. Figure 7a illustrates position trajectory tracking is shown for the three different control including our proposed control law. The blue line, representing the proposed PTCSMAC control’s tracking performance, shows a close adherence to the desired trajectory despite the high-level cyber-attack, indicating the controller’s robustness. In stark contrast, the red and green lines, which represent the tracking by control techniques from references39 and37 respectively, deviate significantly from the reference trajectory. It shows the failure to maintain proper tracking under the high-level cyber-attack (case 3) conditions, with Ming Chen et al.’s method (green line) suffering from singularity in its control law, leading to an inability to follow the trajectory tracking at all. In Fig. 7b we have presented a comparison of the position tracking errors. Our proposed PTCSMAC’s tracking error, depicted by the blue line, remains very small, which signifies its precision and reliability even when the system is under high-level cyber-attack. The red and green lines illustrate the errors for the methods by references39 and37, respectively. Both of these methods exhibit very large errors due to their failure to compensate for the disturbances introduced by the high-level cyber-attack, rendering them ineffective in this scenario. We also have compared the control effort required by the different control laws in Fig. 7c. Our proposed PTCSMAC’s control effort under the high-level cyber-attack (case 3) conditions, shown by the blue line, indicates a smooth and consistent application of control, suggesting that the PTCSMAC can counteract the cyber-attack effects without demanding excessive energy or causing erratic system behavior. In comparison, the control efforts by references37,39, shown by the red and green lines, are likely erratic or inadequate, as these controls fail post-attack due to the same issues that affect their tracking ability. We can see that under a high-level cyber-attack, the PTCSMAC distinctly outperforms the compared methods by maintaining accurate trajectory tracking with minimal error and a smooth control effort. It shows that our proposed PTCSMAC’s control has strong robustness and ability to withstand cyber-attacks and multiple uncertainties within the system, as distinct to the other referenced methods which fail to maintain control due to singularity issues.
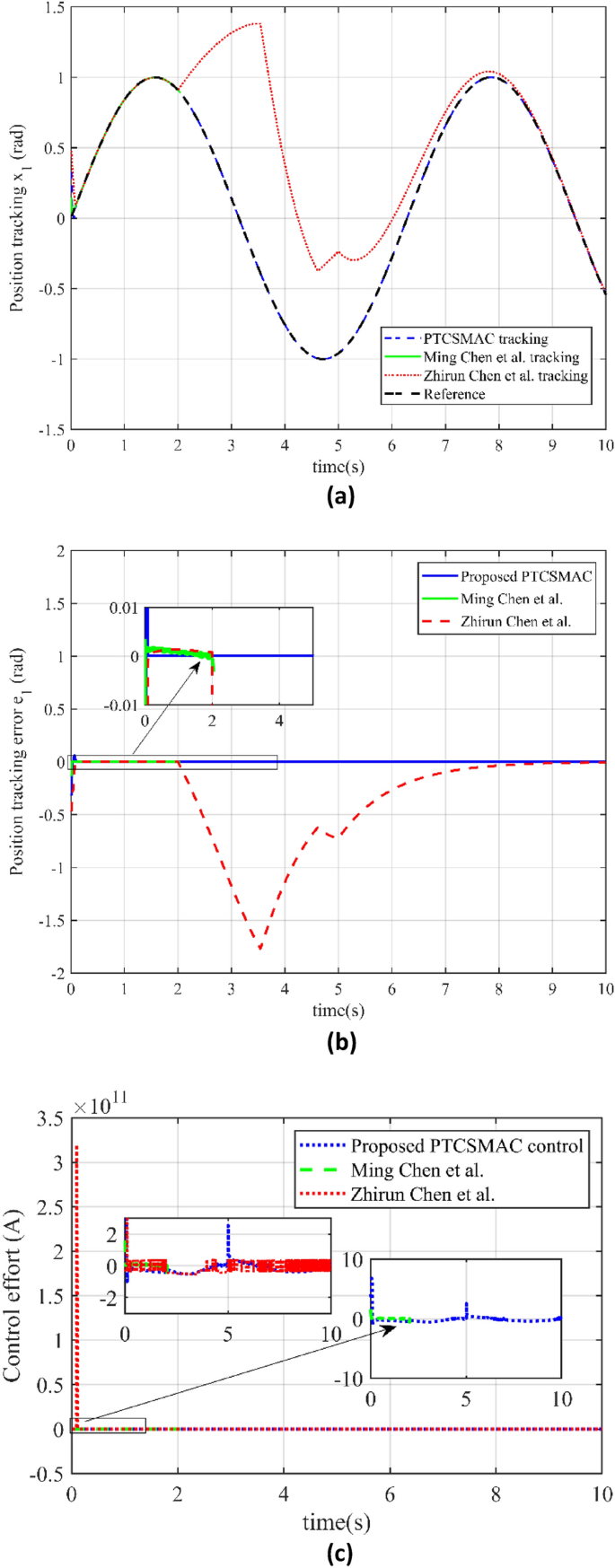
Comparison of tracking and control performance in case 3. (a) Case3: reference trajectory tracking (blue line is our proposed PTCSMAC control tracking, red line is the tracking of Ref39, while green line is the tracking of Ref37). (b) Case3: position tracking error comparison (blue line is our proposed PTCSMAC, red line is the tracking error of Ref39, while green line is the tracking error of Ref37). (c) Case3: control effort comparison of different control laws (blue line is our proposed PTCSMAC control law, red line is the control effort of Ref39, while green line is the control effort of Ref37).
Predefined time impact on the system resilience against cyberattacks
We will analyze the seeker servo system’s performance utilizing our PTCSMAC control over a range of specified times, Ts = 1 s, Ts = 1.2 s, Ts = 2 s, and Ts = 3 s (see Table 3), in this section. Three different scenarios will be used to conduct this evaluation: Case 1, which will be an attack-free case; Case 2, which will be a low-level cyberattack; and Case 3, which will be a high-level cyberattack. Our goal is to measure the tracking inaccuracy in every scenario and evaluate the accuracy and dependability of the PTCSMAC’s position tracking capability. The study will concentrate on how the various predefined time impact the system’s resilience to cyberattacks and tracking accuracy, offering valuable insights into the best configurations for servo position control under varying threat scenarios.
In this section we have analyzed the performance of a seeker servo system utilizing a predefined time convergence sliding mode adaptive controller (PTCSMAC) with various predefined time settings Ts = 1 s, Ts = 1.2 s, Ts = 2 s, and Ts = 3 s across three different cases, each representing varying levels of cyber threat. In Case 1 (attack-free scenario), the results for different Ts values are analyzed in terms of reference versus output position trajectory tracking Fig. 8a. As it can be seen from Fig. 8b the error perfectly converges up to micro level for all the predefined time. The PTCSMAC tracking of the position are shown in Fig. 8c as well as Fig. 8e to achieve perfect tracking across all predefined times, with the associated tracking error remaining minimal, which is crucial for high-precision control. Furthermore, in Case 2, which involves a low-level cyber-attack, the system’s resilience is tested. Despite the adversarial conditions, the tracking Fig. 8c remains accurate for all predefined times, and the tracking error in Fig. 8d is consistently small, demonstrating the control’s effectiveness. And for the Case 3, under a high-level cyber-attack, the robustness of the PTCSMAC is put to the eventual assessment. Under this most challenging scenario, our proposed controller maintains excellent trajectory tracking as depicted in Fig. 8e for all predefined time (Ts) values, and the position tracking error Fig. 8f continues to be negligible. We can analyze that our proposed control law PTCSMAC shows a remarkable capability to ensure precise and accurate position tracking of the seeker servo system, regardless of cyber-attack severity or predefined time settings. The small tracking errors observed in all cases underline the controller’s stability for applications that demand high precision in servo position control under severe cyber-attacks and uncertainties.
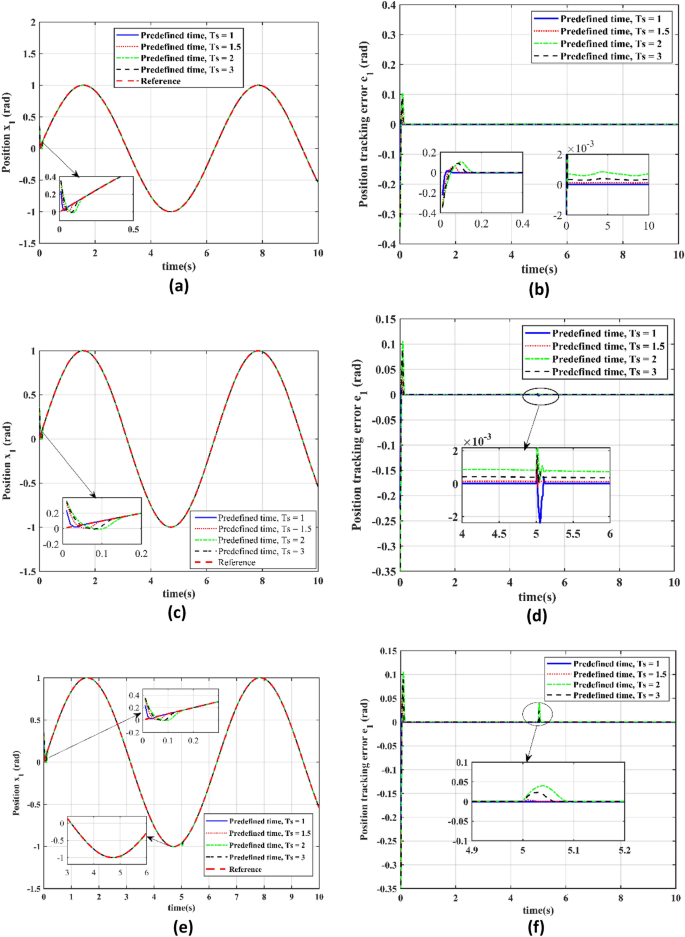
Performance evaluation at different predefined time settings for individual case. (a) Reference v/s output position trajectory tracking for different predefined time (Ts) in case 1. (b) Position tracking error for the different predefined time (Ts) in Case 1. (c) Reference v/s output position trajectory tracking for the different predefined time (Ts) in case 2. (d) Position tracking error for the different predefined time (Ts) in Case 2. (e) Reference trajectory position tracking for the different predefined time (Ts) in case 3. (f) Position tracking error for the different predefined time (Ts) in Case 3.
Control effort for the different cases with dissimilar predefined time settings
In this section our objective is to evaluate the control effort required by the PTCSMAC control law in three different cyber-attack scenarios at different specified time settings (Ts = 1 s, Ts = 1.2 s, Ts = 2 s, and Ts = 3 s) will be covered in the next section. Case 1 is the absence of an attack, Case 2 is a low-level attack, and Case 3 is a high-level attack. The goal is to evaluate how well and consistently the control effort performs under each preset time setting, making sure that the system runs without producing any negative chatter in any scenario. This fast control response is critical to the servo system’s robustness and reliability. The main objective of the analysis is to show that even in the most extreme attack scenarios, the PTCSMAC control law can sustain a consistent and efficient control effort that is resistant to the seriousness of cyberthreats, preserving system performance and stability without the negative consequences of chattering.
Figure 9a–c show how the PTCSMAC control rule performs very well and provides chatter-free control in all predefined time settings under a variety of cyber-attack scenarios. The PTCSMAC’s control effort is smooth and consistent in all scenarios attack-free (Case 1), low-level (Case 2), and high-level (Case 3) which suggests that it is robust and successful. The CPS servo system’s stability and precision depend on this smooth control, which keeps the actuators safe from chattering’s damaging consequences. Together, the results show that our suggested controller not only satisfies the CPS servo system’s high-precision control requirements, but also maintains its efficiency and composure over a variety of predetermined times even in the appearance of the most disruptive cyberthreats proves its superiority in control performance.
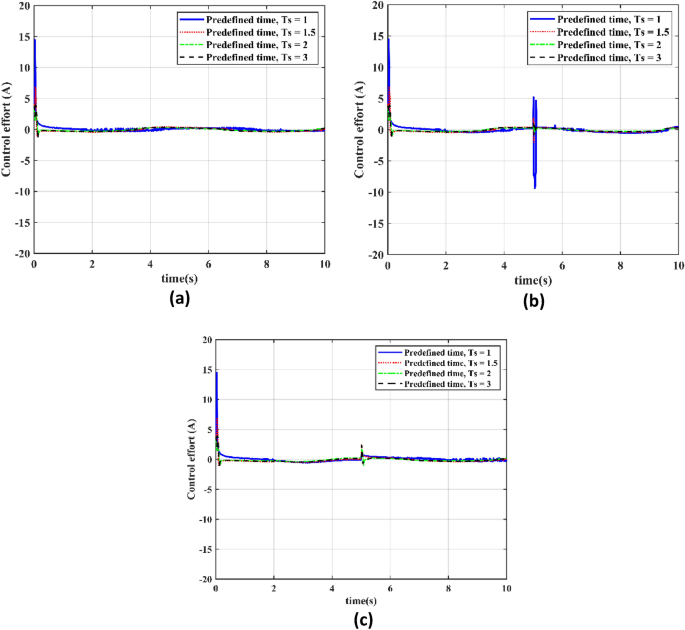
Control effort for the different predefined time settings. (a) Control effort for the different predefined time (Ts) in Case 1. (b) Control effort for the different predefined time in Case 2. (c) Control effort for the different predefined time (Ts) in Case 3.
CPS servo system’s performance analysis under of different activation functions
According to the Table 4, we will use a range of activation functions to conduct an in-depth analysis of the tracking and control performance of the CPS servo system in this section. In particular, we will evaluate how well each activation function performs in maintaining accurate trajectory tracking and seamless control effort in both uncompromised and compromised cyber environments. To determine the advantages and disadvantages of our suggested controller in various functional contexts, the analysis will concentrate on finding any performance imbalances, especially the chattering seen with the Cosine Function in Case 2.
From the above Fig. 10a–f, we can analyze the performance of the CPS servo system under different activation functions, as summarized in Table 4, indicates the system’s adaptability and precision across various mathematical models. These functions include the Sigmoid Function (Sig F), Hyperbolic Tangent Function (HTF), Hard Limit Function (HLF), and Cosine Fourier Basis Function (CF cos). The capability of the proposed control to track the desired output trajectory in an attack-free scenario (Case 1) and under cyberattack conditions (Case 2) is evaluated for each activation function. According to our findings presented in Fig. 10, the proposed controller consistently achieves high precision in position tracking for all activation functions, even in severe conditions such as a high-level cyberattack. The control effort remains smooth and free from chattering in all cases, with the exception noted in Fig. 10d for the Cosine Function during Case 2, where some irregularity is observed. Regardless of this exception, our proposed PTCSMAC controller’s performance with different activation functions suggests a robust and versatile design, capable of maintaining CPS servo position control system integrity and precision across a range of operational settings.
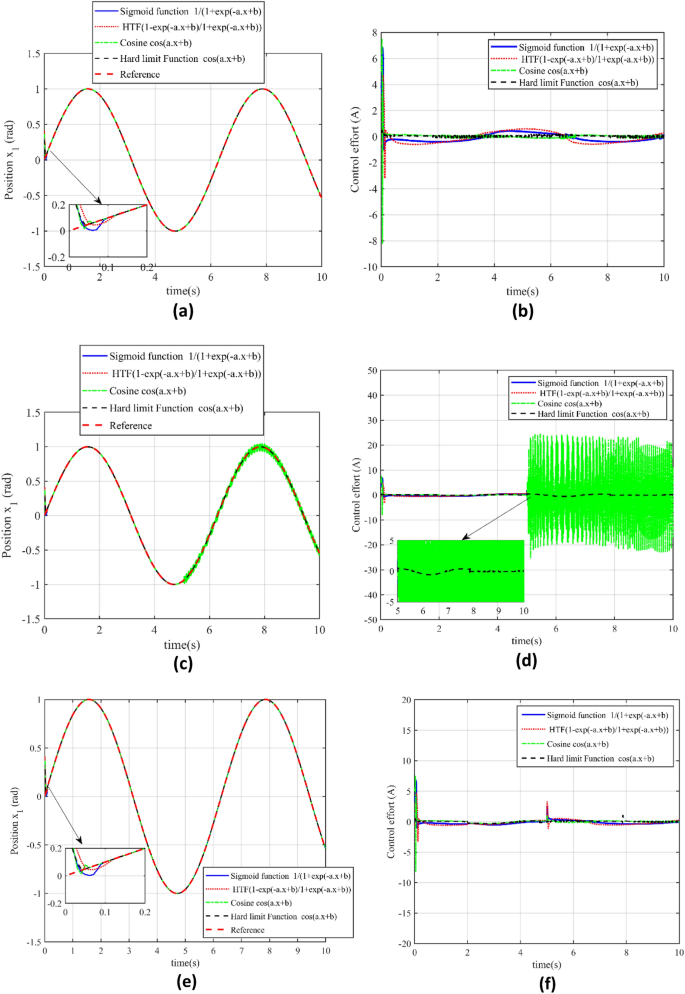
Performance and evaluation of the different activation functions. (a) Reference v/s output trajectory tracking for different activation functions in case 1. (b) Control effort for the different activation functions in Case 1. (c) Reference v/s output trajectory tracking for the different activation functions in case 2. (d) Control effort for the different activation functions in Case 2. (e) Reference trajectory tracking for the different activation functions in case 3. (f) Control effort for the different activation functions in Case 3.
Tracking error analysis for the different activation functions in each case
In this section we have demonstrated the error evaluation formulas to assess performance criterion such as Integral square error ,\({\text{ISE }} = \int e
Source link